What happens in movies or TV series may never happen in real life. In fact, when it comes to break-ins, robberies, or hacker attacks, movies are full of completely unrealistic things. Often, the highly specialized technicians are not even involved in the filming process to provide proper guidance. That’s how the audience is getting lost in a distorting reality while the experts are painfully confused about such fakes. For instance, the viewers believe some powder can detect IR rays that protect the Holy Grail. Or, they think a burglar can connect a wire to the Ajax keypad, read the password, and hack the security system.
We’ve analyzed probably the most popular movie break-in — hacking a security system through a keypad.
As a rule, it is performed in three main steps:
- Finding a keypad;
- Gaining physical access or intercepting a radio signal;
- Hacking the system through third-party software.
Let’s find out what is wrong with each step.
Step 1: Finding a keypad
The first move in any intrusion attempt is gathering information. When movie intruders enter a building, they know exactly which direction to run and where to look for potentially hackable devices, even if they are on the other side of the wall. While it may seem simple in theory, it is actually quite difficult to distinguish between wired and wireless devices in practice.
To determine the exact location of the wired keypad, an intruder must use a high-powered multiscanner to find the right cable hidden in the wall. However, the multiscanner does not identify what kind of cables these are — related to a doorbell, door intercom, or electrical wiring. And with thick walls, a multiscanner can be fully useless. If the keypad is wireless, searching for cables hidden in the wall won’t help.

Intruders can try to scan the radio signal to detect the location of the wireless device. Still, the device is allotted a short time frame to exchange data with a hub using the TDMA technology. The rest of the time, their communication modules are inactive. To an intruder, it may take dozens of minutes to pinpoint the signal’s source. And even then, there’s no guarantee that the detected signal source belongs to the intended device. In addition, it might not be an Ajax device, as other devices also use Ajax frequencies.
However, to catch the radio signal, intruders use a code grabber. A special device intercepts the signal transmitted when the system is armed or disarmed. But still, it is impossible to hack an Ajax device in this way due to the signal encryption and a proprietary communication protocol.
Learn more about Jeweller radio protocol
Protection technologies:
- block encryption featuring a dynamic key,
- TDMA principle.
Step 2: Physical access
To attack the security system, intruders always look for physical access to the device. Gaining access should be fast and quiet, even if it needs to drill through a half-meter wall.
As a rule, keypads are installed at the entrance. Usually, these are load-bearing walls made of brick, concrete, or reinforced concrete with a thickness of 25 cm or more (depending on the building codes and regulations). Sometimes, it can reach 50 cm, and drilling through it silently in a few seconds is impossible.
In addition to attracting the attention of neighbors, there is a risk of damaging the device with a drill. The Fibra line of the wired keypad runs through the cable channel in the SmartBracket mounting panel. Channels have a curved construction, and the cable is fixed with ties. That is why, if intruders drill SmartBracket, they would probably cut off all the wires.
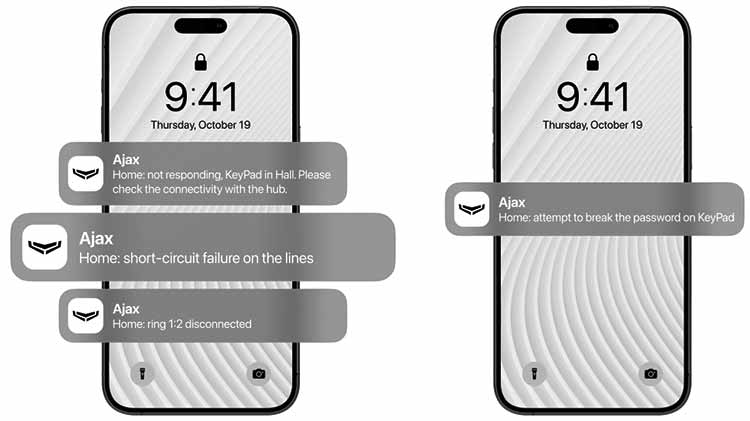
Besides damaging the device, users and the Central Monitoring Station (CMS) will be notified of the intrusion attempt. If the cable is damaged, they will receive notifications about a short circuit and ring connection break (if the Ring topology is used). In the case of the cable breaking or the keypad damage, a notification about the loss of communication with the hub will also be received.
Learn more about Fibra technology

Even if an intruder tries to damage the security system with electrical sabotage (e.g., using a stun gun), LineProtect Fibra will absorb the impact. All devices between LineProtect and the hub will continue to operate.
LineProtect Fibra is a module to protect Ajax hubs and wired devices from sabotage when an intruder causes short circuits, applies 110/230 V~, or uses stun guns. The module monitors the input and output voltage on the Fibra line. If LineProtect detects an abnormal voltage on the line, it activates the fuses and cuts off the power supply to the devices installed between LineProtect and the hub. Wireless keypads simply have no wires. Moreover, there are no wires inside wireless and even wired Ajax keypad enclosures. So, it’s impossible to connect to any wire inside the devices. The only available wire is an isolated and hidden Fibra cable.
Some movie intruders tear the keypad off the wall and break it, causing the security system to fail. However, the keypad is just a part of the system but not its “brain”. So, damaging a keypad doesn’t make much sense for compromising the overall security. In addition, the Ajax keypads have a tamper that notifies users and the CMS in case of opening the device enclosure, removing the device from the mounting panel, or detaching it from the surface.
Protection technologies:
- instant notifications,
- communication loss detection,
- tamper alarm,
- LineProtect Fibra,
- ring connection.
Step 3: Hacking
Assume that an intruder has connected to the keypad and left undetected by the system. As it’s possible only with Fibra, let’s explore this case. Connecting to a single wire, as shown in movies or TV series, makes no sense because the Fibra line has four wires: two signal wires and two power wires.
To protect the transmitted data, Fibra uses encryption featuring a dynamic key. Hacking and getting to the data will take the capabilities of a supercomputer and an investment of weeks or even years. In other words, it is a futile effort. However, even encrypted data still needs to be reached. Each communication session between a hub and a device begins with authentication: unique markers and properties are compared. If at least one parameter fails the verification, a hub ignores the device commands. Therefore, there is no point in tampering or intercepting data.

The keypad does not store user codes, making it unachievable to obtain codes from it. When the user enters the code, it is sent to the hub in encrypted form, and the hub verifies it. Codes within the hub are stored securely in a hashed form, and the Ajax hub uses the OS Malevich real-time operating system, providing immunity to viruses and cyberattacks. It is also impossible to guess the code using a brute-force attack. If an incorrect code is entered or a non-verified access device is used three times in a row within a minute, the keypad will be locked for the time specified in its settings. During this time, the hub will ignore all codes and access devices while informing the security system users and the CMS about attempted unauthorized access. Finally, it is impossible to break-in undetected. Any disarming of the system is logged, and users and the CMS will receive a notification about it. No one can remove a notification from the hub’s event feed. In addition, if the CMS monitors the time the system is normally armed and disarmed, the operator calls the user when the system is disarmed at an unplanned time.
Protection technologies:
- encrypted proprietary communication protocol,
- protection against spoofing,
- auto-lock against unauthorized access.
Conclusions
In conclusion, hacking an Ajax system is a tough challenge. The data is protected by encryption, and the keypad doesn’t store codes. The hub checks every command, filtering out unauthorized access attempts. Traditional brute-force attacks are rendered impossible due to the keypad’s auto-lock feature. What unfolds in movies, TV series, or advertisements adheres to the laws of drama, often deviating from the principles of physics and mathematics. However, even in this realm, we can offer a spoiler: try to be skeptical of everything you see in movies.

